
Secure Data Transmission And Encryption: Lock With Binary Code Texture Surrounded By Flying Mails Stock Photo, Picture And Royalty Free Image. Image 40357700.
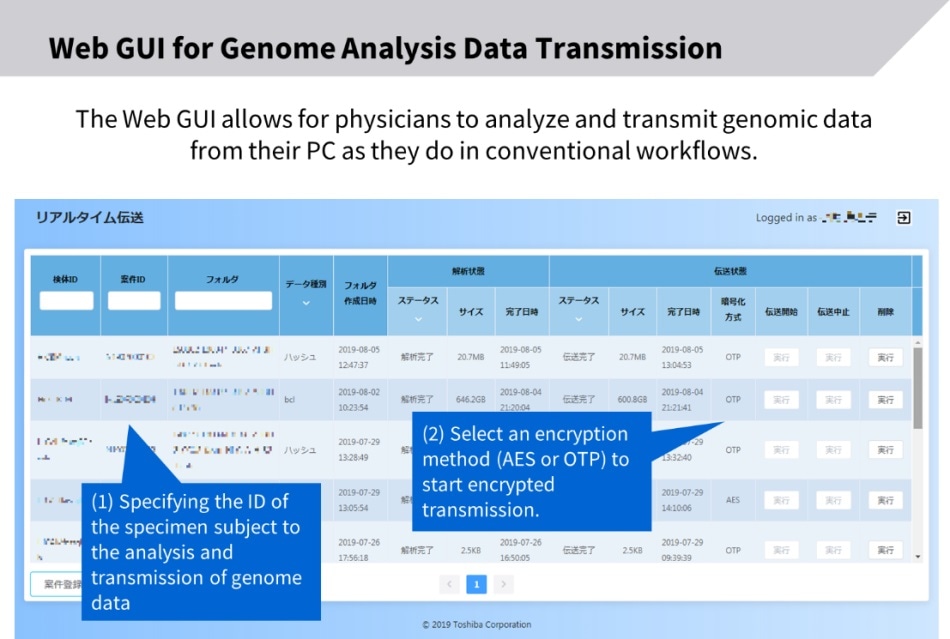
Quantum cryptographic communications technology can provide safe, secure data transmission in genomic medicine

Framework outline of secure data transmission in cloud-based smart city. | Download Scientific Diagram

Secure Data Transmission And Encryption: Lock With Binary Code Texture Surrounded By Flying Mails Stock Photo, Picture And Royalty Free Image. Image 40358218.

Analysis of Encryption and Lossless Compression Techniques for Secure Data Transmission | Semantic Scholar

Secure Data Transmission And Encryption: Lock With Binary Code Texture Surrounded By Flying Mails Stock Photo, Picture And Royalty Free Image. Image 40358213.
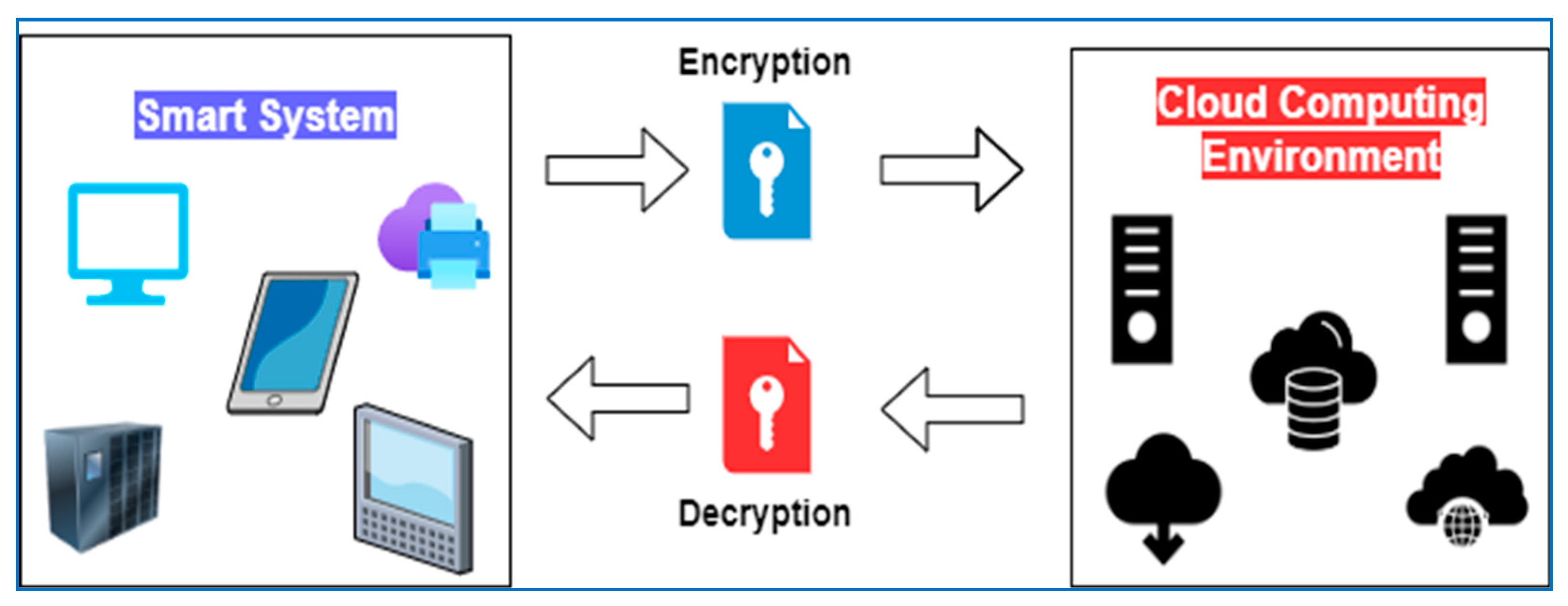
Symmetry | Free Full-Text | Encryption Techniques for Smart Systems Data Security Offloaded to the Cloud

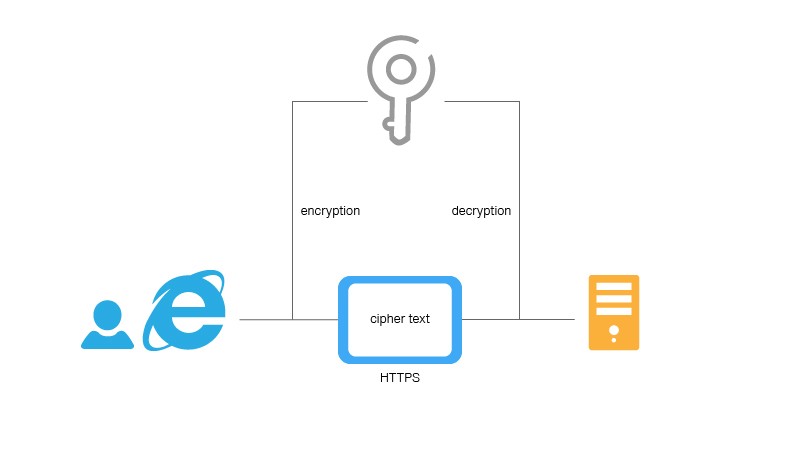

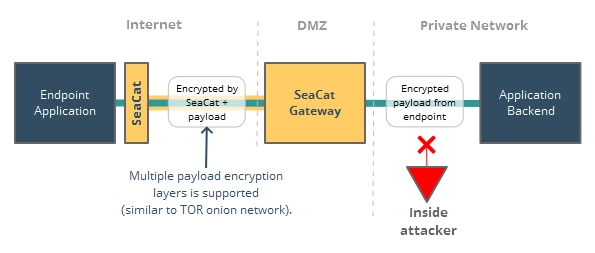
![PDF] SECURE DATA TRANSMISSION USING STEGANOGRAPHY AND ENCRYPTION TECHNIQUE | Semantic Scholar PDF] SECURE DATA TRANSMISSION USING STEGANOGRAPHY AND ENCRYPTION TECHNIQUE | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e53eec0df772f13bbac83f3722ad64206faeab65/5-Figure1-1.png)








![3 Ways] Big Data Encrypted Transmission Methods 3 Ways] Big Data Encrypted Transmission Methods](https://images.ctfassets.net/bg6mjhdcqk2h/78o0ciUwrq8qQ67Yoey8fn/1dede116b8ef4ca5369499c8c33f42bb/3-ways-big-data-encrypted-transmission-methods.png)