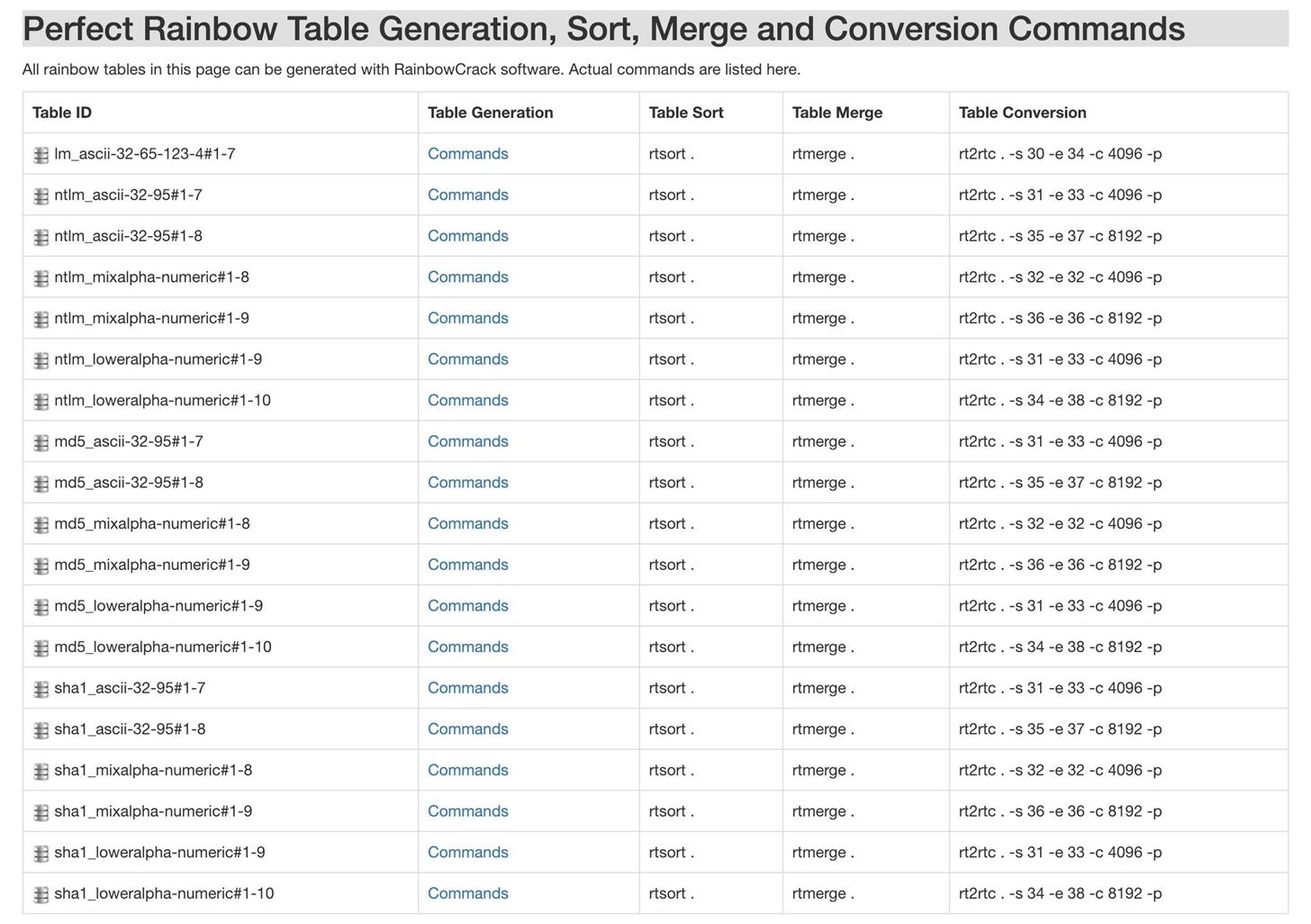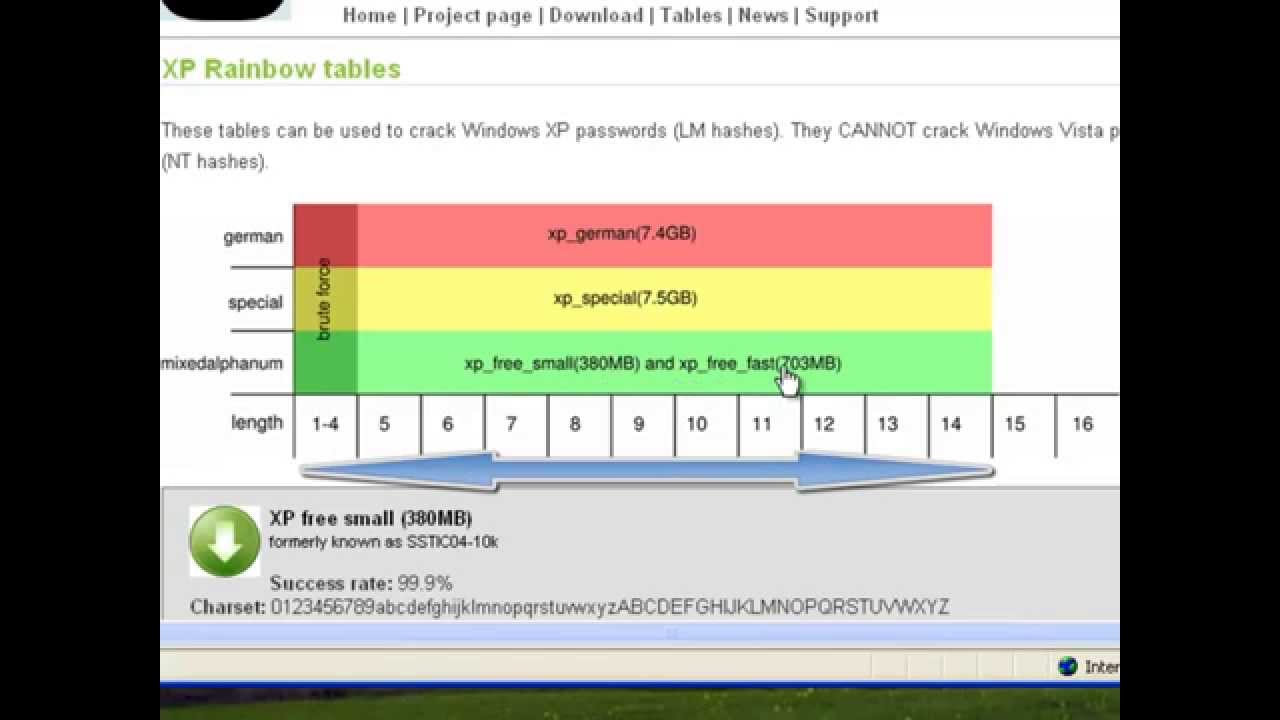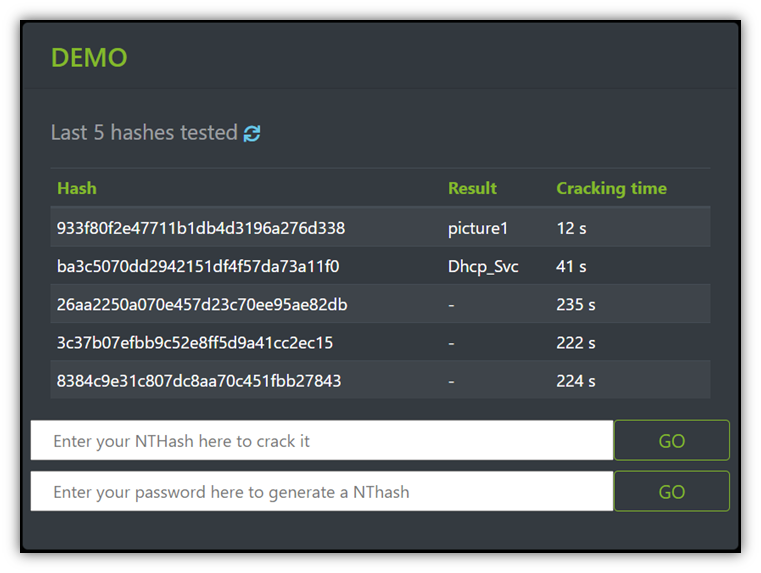
RainbowCrack & How To Use Rainbow Crack With Rainbow Tables - Darknet - Hacking Tools, Hacker News & Cyber Security

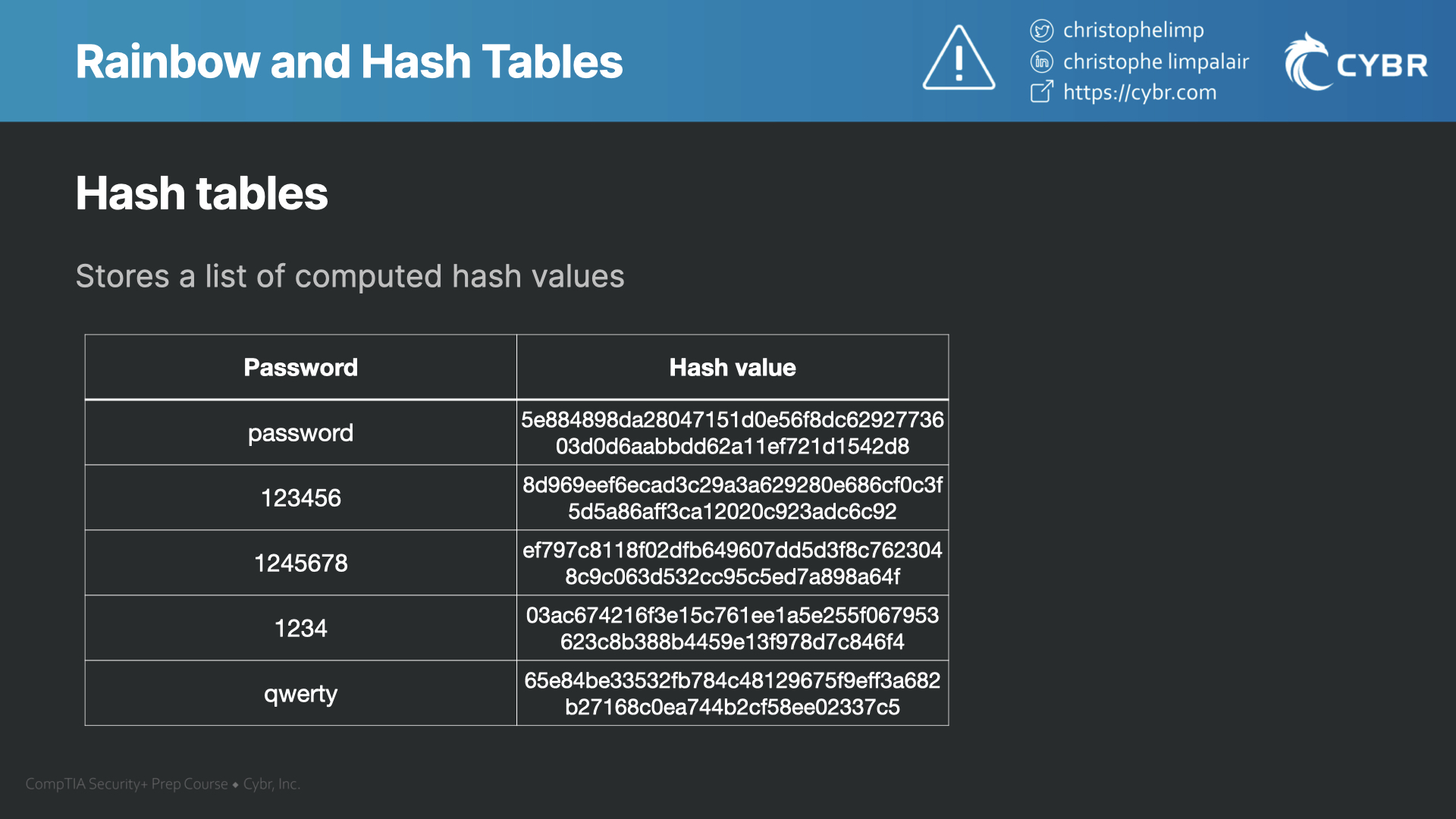
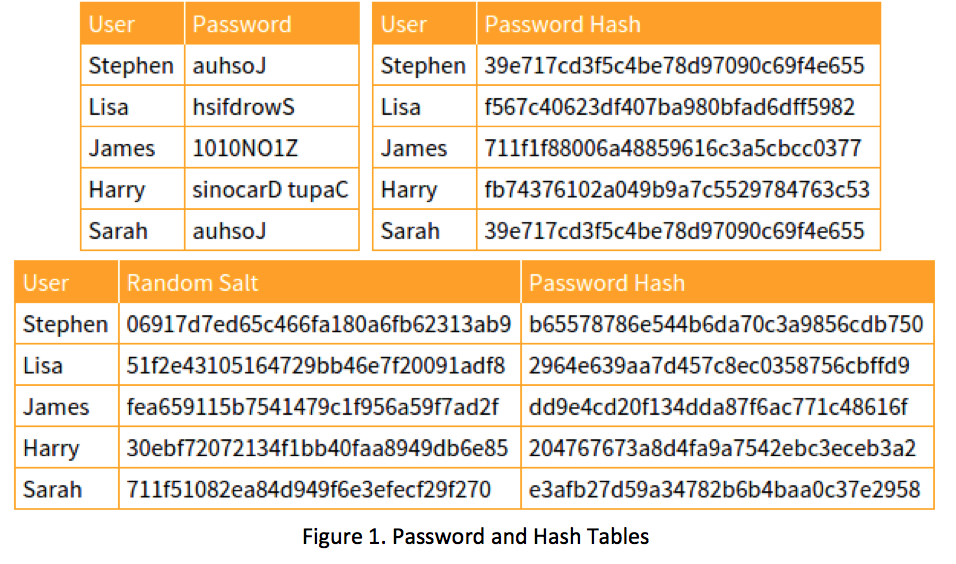
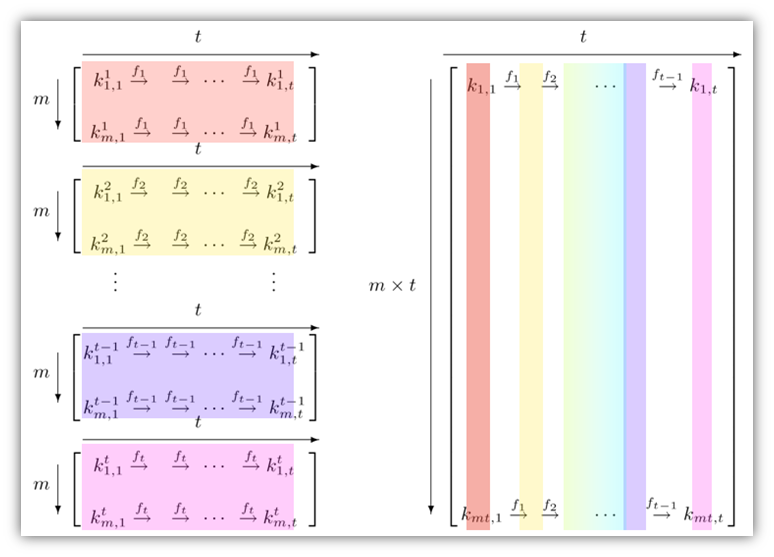
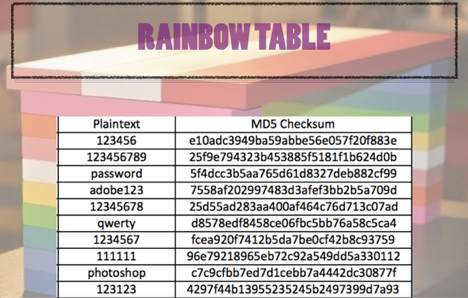
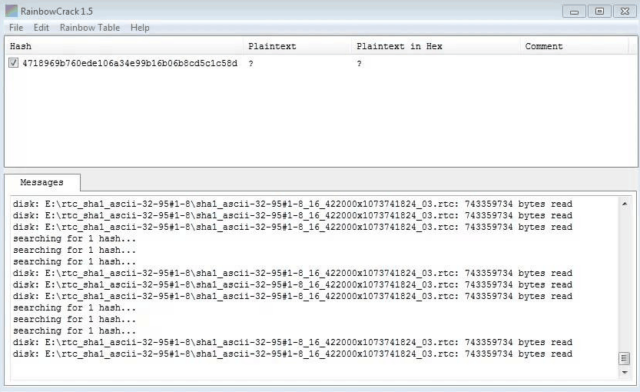
Magic Password - What is a rainbow table attack? It is a type of hacking wherein the hacker tries to use a rainbow hash table to crack the passwords stored in a
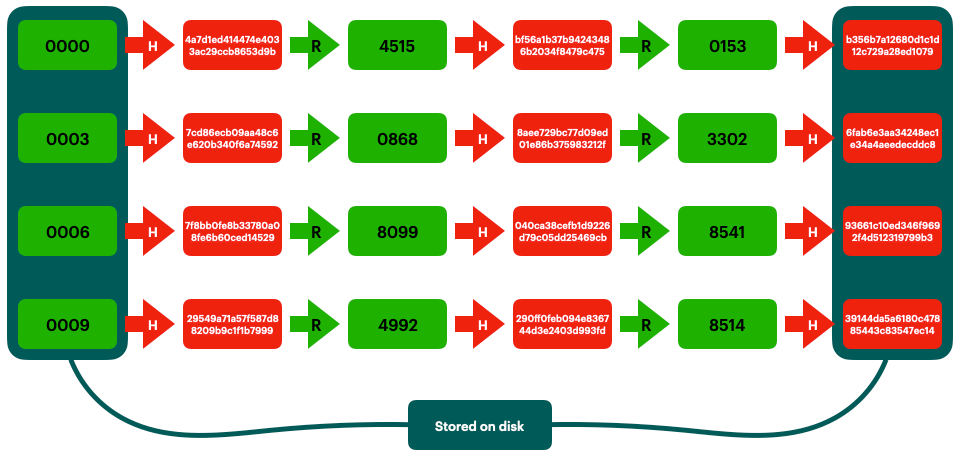
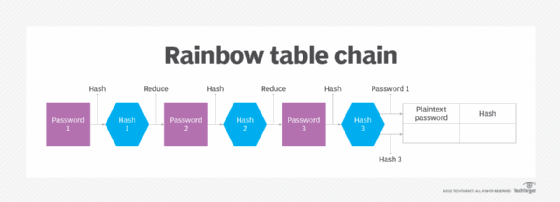
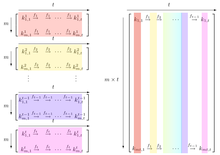
Rainbow Tables (probably) aren't what you think — Part 1: Precomputed Hash Chains | by Ryan Sheasby | Medium